Self-hosted deployment
Deploy on Azure
Generate and manage your reports inside your own Azure environnement using Container Apps
Introduction
Deploying Carbone in an Azure Container Apps environment is a very simple and effective way of implementing high-performance document generation while respecting your security and operation processes.
By default, the program runs with free Community features. To use Carbone Enterprise Edition, you need a Carbone license. Contact us to learn more, or request a free 30-day trial in our chat.
Quickstart
Create Azure storage for persistent data
1. Create Storage accounts for Carbone
Go to Storage accounts section in Azure portal and click on Create:
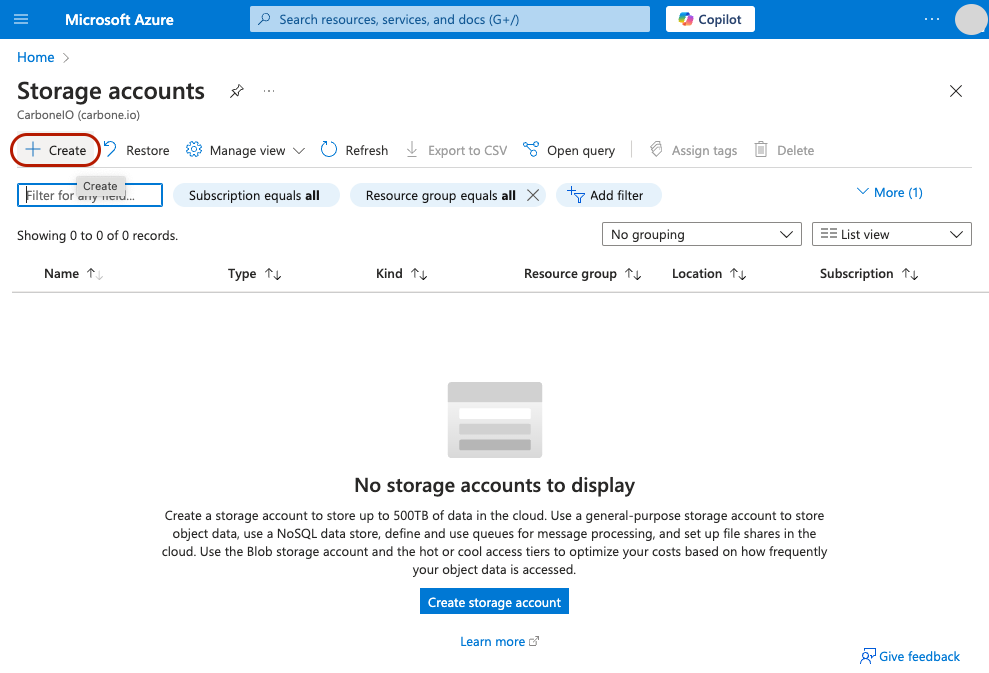
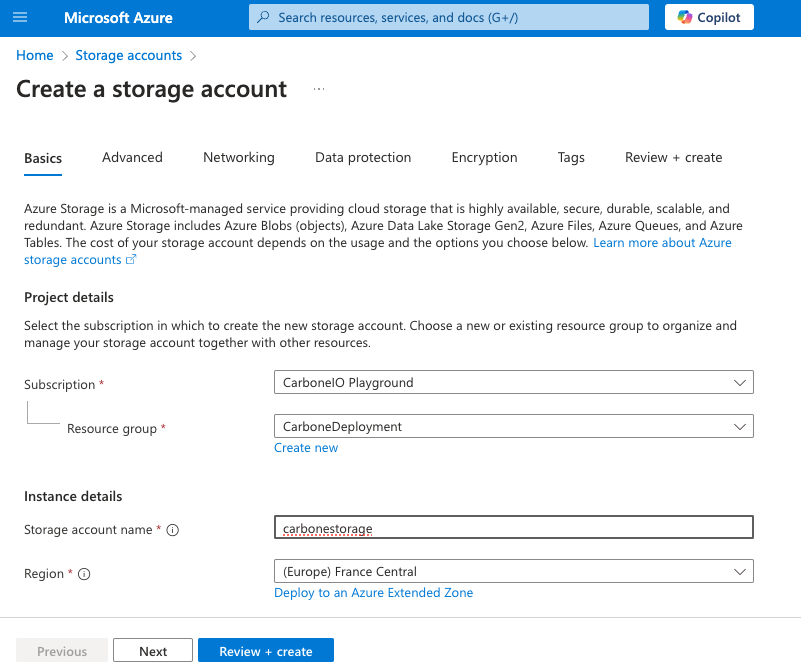
Then set storage name, following carbonestorage, click on Review + create and Create again:
2. Create Template and Render containers
When the Storage Account creation is finalized, you can create 2 containers.
Click on Create in Data storage / Containers section :
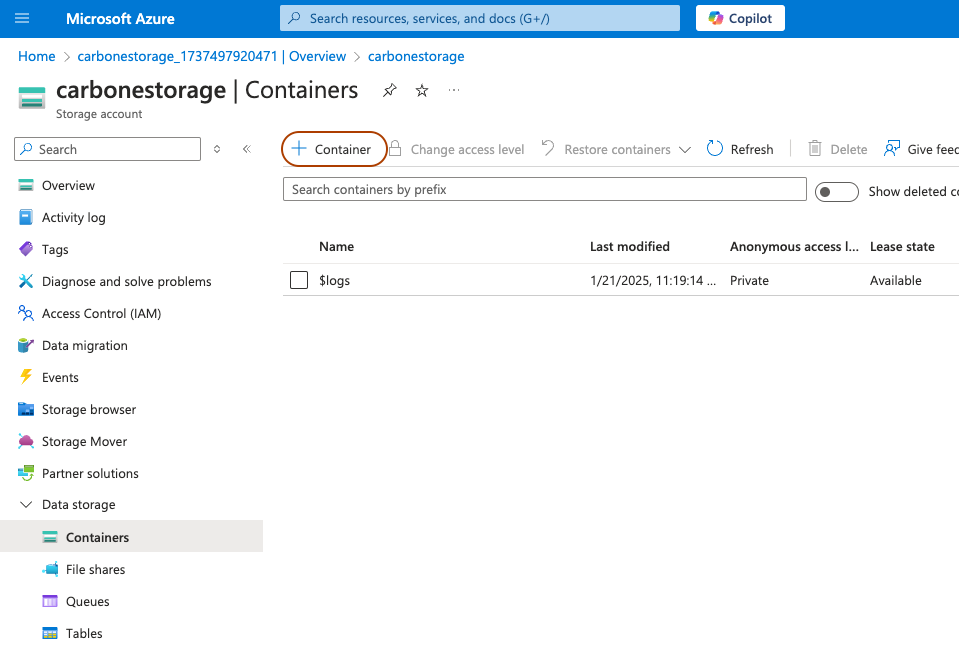
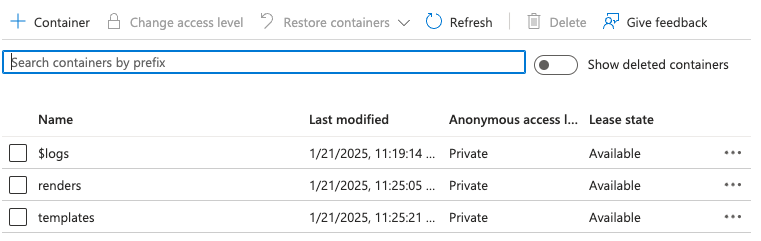
Then, create 2 containers : templatesand renders.
3. Get credentials
Finally, you need to get Storage Account Name and Account key form Azure portail. Go to Security + Network / Access Key settings.
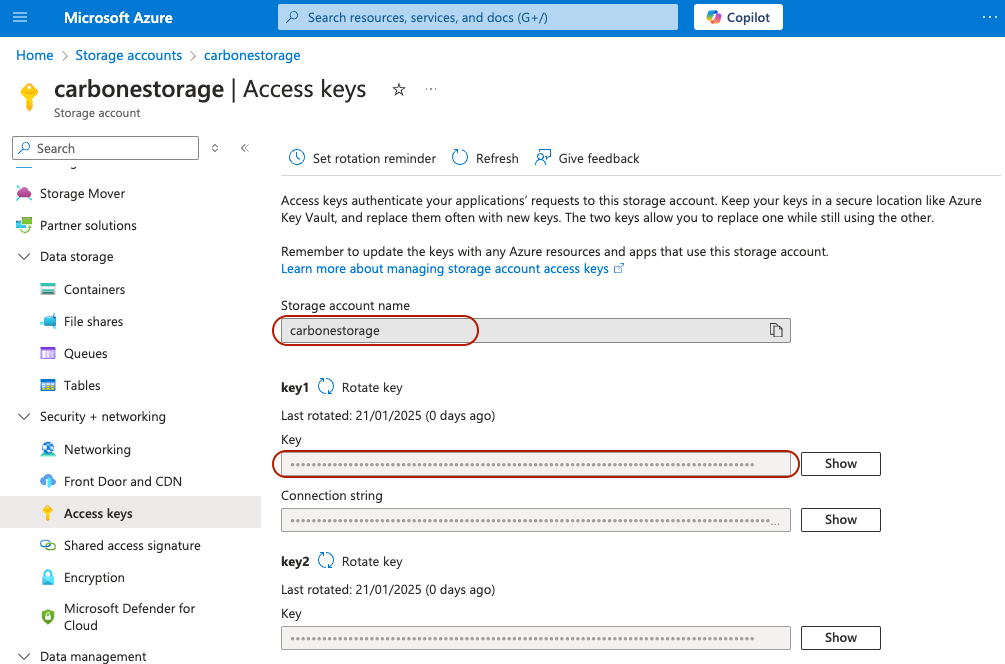
Keep these two values for the next step.
Create Carbone service
Go to Container Apps portail, and Create new Container App:
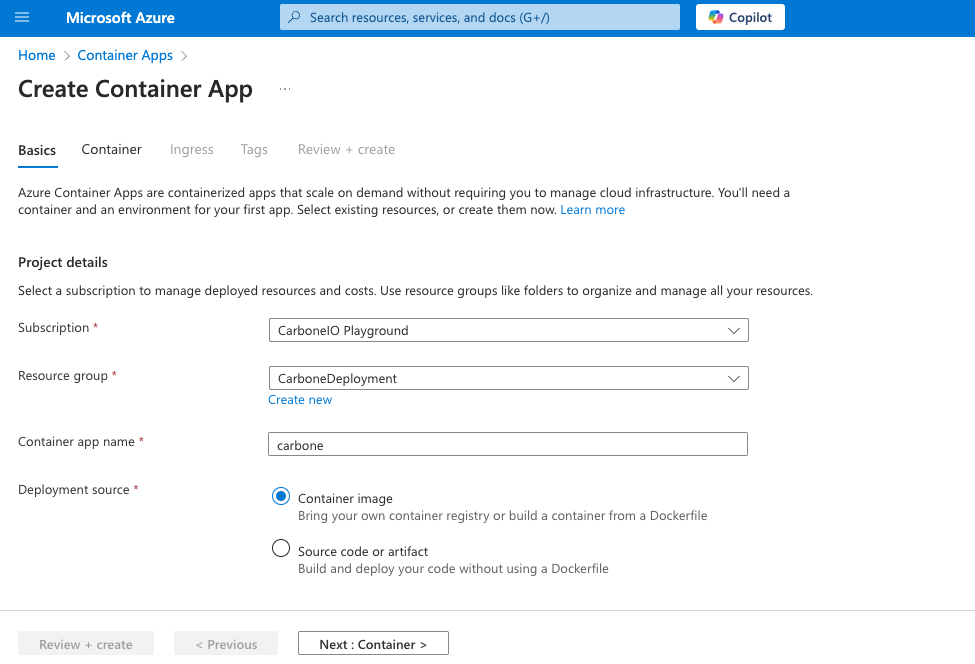
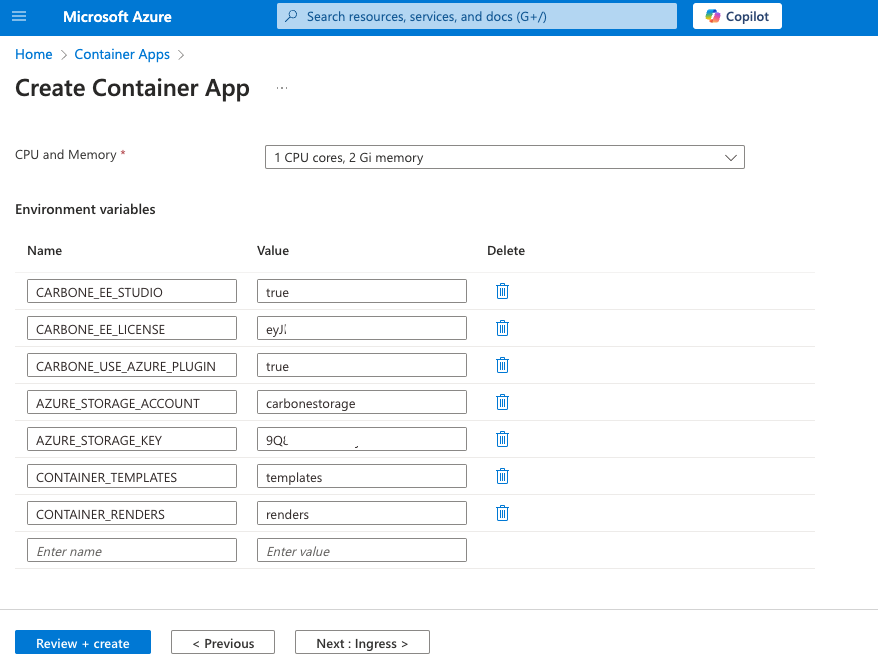
Create container carbone with following configuration.
Basic
- Container app name : carbone
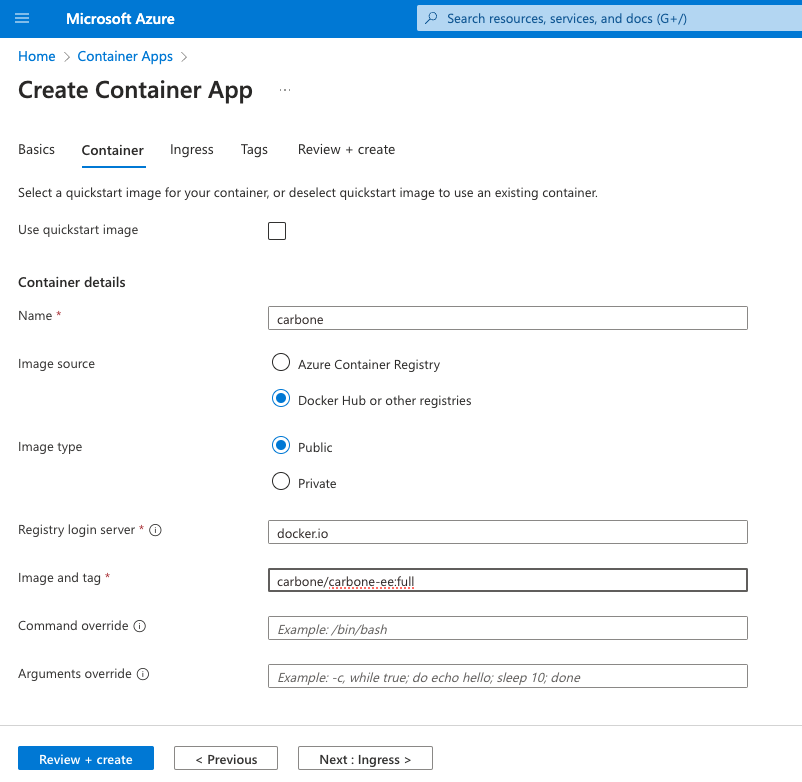
Container
- Image source : Docker Hub
- Image tag :
carbone/carbone-ee:full - CPU and Memory : 1vCPU, 2Gi memory
- Environnement variable :
CARBONE_EE_LICENSEwith you license to enable Enterprise featuresCARBONE_USE_AZURE_PLUGIN=trueAZURE_STORAGE_ACCOUNTwith Storage Account,carbonestoragein this exampleAZURE_STORAGE_KEYwith key from previous stepCONTAINER_TEMPLATEStemplate storage container nameCONTAINER_RENDERStemplate storage container name
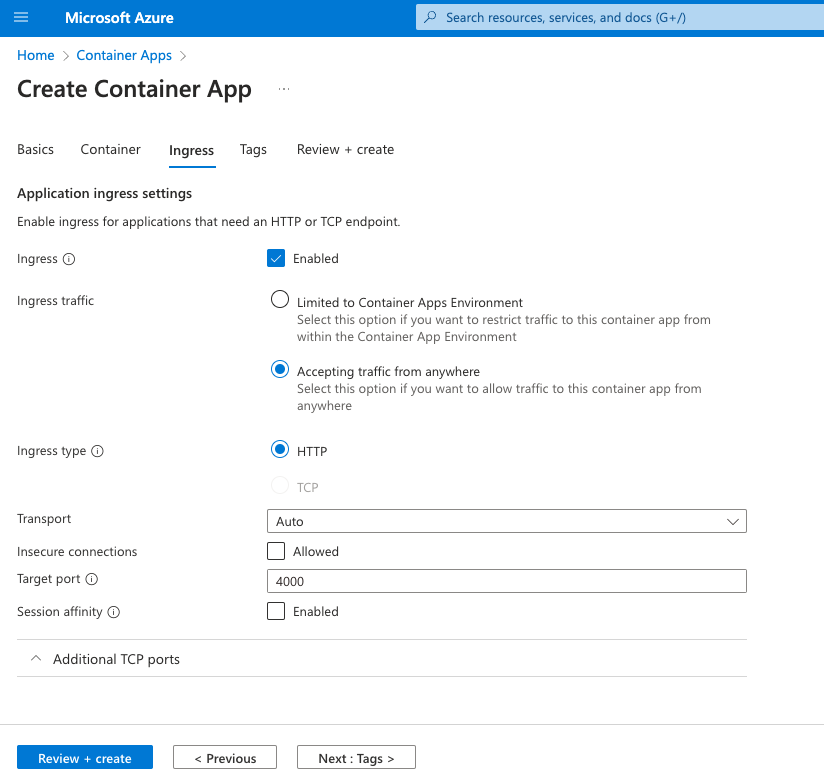
Ingress
For test simple setup, enable full access and set port to 4000:
Enjoy Carbone
Your service is then available via the url of your Container App.
Configuration
Template and Render storage
As indicated in the quick start section, we recommend that you configure the Azure Blob Storage plugin to store rendering templates.
To do this, set the CARBONE_USE_AZURE_PLUGIN environment variable to true, then configure the variables below.
Azure Blob Storage Configuration
AZURE_STORAGE_ACCOUNT: Storage Account NameAZURE_STORAGE_KEY: Storage Account KeyCONTAINER_TEMPLATES: Templates Storage NameCONTAINER_RENDERS: Renders Storage Name
Enable Studio
Just set CARBONE_EE_STUDIO to true to enable Carbone Studio on your instance.
Authentication
To enable API authentication, you need to follow these steps :
- Set CARBONE_EE_AUTHENTICATION to true
- Generate private/public Carbone Key
The key generation tool is included in the docker image from Carbone version 5 onwards.
docker run -it --platform "linux/amd64" carbone/carbone-ee:slim-5.0.0-beta.0 generate-keysThe two keys will be generated and displayed in the console.
Conservez le contenu de la clé privé de manière sécurisé. Pour la clé publique, nous vous recommandons de la stocker dans le Key vaults Azure puis de monter ce secret sur vos containers Carbone sur le fichier /app/config/key.pub.
- Generate JWT token
Follow interactive shell :
docker run -it --platform "linux/amd64" carbone/carbone-ee:slim-5.0.0-beta.0 generate-token
## Paste in terminal content of key.pemA JWT token is then displayed in the console. You can then use it in your API calls.
Terraform sample deployement
Carbone autoscaling deployment with secret storage
A complete terraform deployment example is available.
